Public Access for Managed Databases and Storage
Today we are excited to announce public network support for Northflank Addons (databases such as MySQL, PostgreSQL, MongoDB & Redis and S3 compatible MinIO storage).
- Connect to your databases outside of Northflank
- Easily connect to popular tooling such as Retool, Segment and database UIs without needing to use Northflank CLI proxy
- External access is routed via Northflank’s highly performant DNS and load-balancers
- Traffic is encrypted end-to-end with TLS from client to the database
- Fine-grained network access controls for increased security
Northflank continues to level up the DBaaS experience across multiple popular OSS databases with consistent capability. You are now able to access your addons securely within the same project, via northflank forward and now for production workloads via load-balancers when workloads are deployed externally.
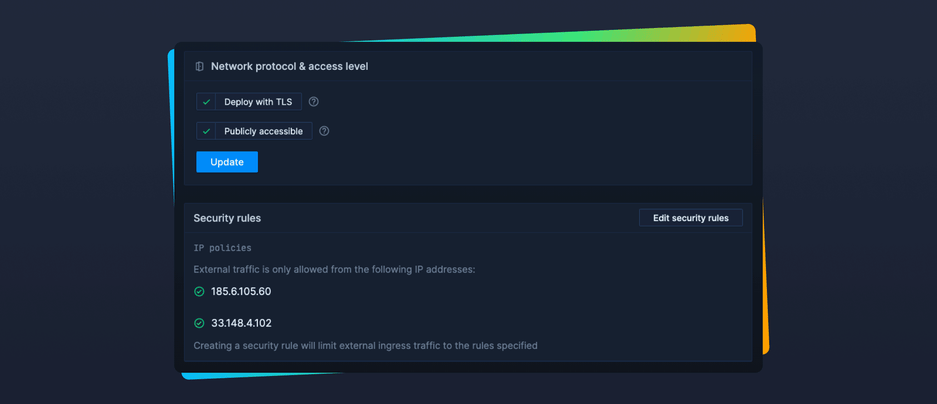
Public access can be enabled on addons deployed with TLS which can be configured in Network Settings. Once enabled, you will notice new external connection strings in Connection Details. You can configure them to be automatically inherited from your jobs and services.
Configurable security rules are also included in this release. Similar to IP and Basic Auth security rules that are available for services, you can specify certain IP addresses from which external ingress traffic will be allowed. We recommend always configuring IP policies as this brings another layer of security to your data.

Example connection scripts
// Connect to a publicly accessible MongoDB with inherited environment variables
// Inherit 'EXTERNAL_SRV' and 'DATABASE' via a Secret Group
import MongoClient from 'mongodb'
let db = {}
let client = {}
const MONGO_CONNECTION_STRING = process.env.EXTERNAL_SRV
const MONGO_DATABASE = process.env.DATABASE
const INIT_MONGODB = async () => {
try {
console.log('Connecting to database')
client = await MongoClient.connect(MONGO_CONNECTION_STRING, { useUnifiedTopology: true });
db = client.db(MONGO_DATABASE)
console.log('Connected to database');
} catch (err) {
console.log(err);
}
}
export default async () => {
await INIT_MONGODB();
}
export { db, client }// Connect to a publicly accessible PostgreSQL with inherited environment variables
// Inherit 'EXTERNAL_POSTGRES_URI' via a Secret Group
import pg from 'pg'
const { Pool } = pg;
const POSTGRESQL_CONNECTION_STRING = process.env.EXTERNAL_POSTGRES_URI
let client = {};
const pool = new Pool({
connectionString: POSTGRESQL_CONNECTION_STRING,
})
const INIT_POSTGRES = async () => {
try {
console.log('Connecting to database');
client = await pool.connect();
console.log('Connected to database');
} catch (err) {
console.log(err);
}
};
export default async () => {
await INIT_POSTGRES();
}
export { client }// Connect to a publicly accessible Redis with inherited environment variables
// Inherit 'HOST' and 'REDIS_MASTER_URL' via a Secret Group
import redis from 'redis'
const REDIS_CONNECTION_STRING = process.env.REDIS_MASTER_URL
const REDIS_HOST = process.env.HOST
let client = redis.createClient({url: REDIS_CONNECTION_STRING, tls: {
servername: REDIS_HOST
}});
const INIT_REDIS = async () => {
try {
console.log('Connecting to database');
await client.on('connect', function() {
console.log('Connected to database');
});
} catch (err) {
console.log(err);
}
};
export default async () => {
await INIT_REDIS();
}
export { client }