

What is multi-tenant cloud deployment? A complete guide for 2026
Multi-tenant cloud deployment is the process of deploying applications that serve multiple customers (tenants) on shared cloud infrastructure while maintaining strict isolation between them.
Here's what you need to know:
- The deployment challenge: Unlike single-tenant systems, you need to handle automated tenant provisioning, resource isolation, per-tenant scaling, and compliance requirements, all while keeping operational overhead manageable.
- Your deployment options: You can deploy on shared infrastructure (cost-efficient), partitioned resources (balanced approach), or dedicated infrastructure per tenant (maximum isolation). Most production systems use a hybrid approach based on customer tier.
- The operational complexity: Managing tenant lifecycle, cost allocation, network isolation, and disaster recovery across dozens or hundreds of tenants requires significant automation and tooling.
- How platforms help: Solutions like Northflank automate multi-tenant deployment by providing instant tenant isolation, BYOC (Bring Your Own Cloud) support across cloud providers, and built-in security, letting you deploy production-ready multi-tenant environments in minutes instead of weeks.
Let's break down how multi-tenant cloud deployment works and what you need to get it right.
You've designed your multi-tenant architecture with separate schemas, namespace isolation, or dedicated databases per tenant. Now you need to deploy this system to production cloud infrastructure.
Multi-tenant cloud deployment is the process of taking your multi-tenant application and deploying it across cloud infrastructure (AWS, GCP, Azure, or your own hardware) in a way that keeps tenants isolated while maximizing resource efficiency.
Here's what makes it different from deploying a regular application:
- Tenant provisioning at scale: You need automated systems to spin up new tenant environments (namespaces, databases, configs) without manual intervention
- Infrastructure isolation decisions: You're choosing between shared compute (cost-efficient but needs careful isolation), partitioned infrastructure (balanced approach), or fully dedicated resources per tenant (maximum isolation but higher cost).
- Deployment across boundaries: Your tenants might need to be deployed in different regions for data residency, or across multiple cloud providers for compliance requirements.
Getting the isolation right while avoiding the operational overhead of managing dozens of separate deployments manually is the core challenge.
Your deployment model determines how you balance cost, isolation, and operational complexity. There are three main approaches, and most production systems use a combination of them.
All tenants run on the same compute, networking, and storage resources. You're using namespaces, RBAC, and network policies to create logical boundaries between tenants.
This works well for internal teams or early-stage SaaS customers who don't need physical isolation. Your costs stay low because you're maximizing resource utilization.
Each tenant gets dedicated resources within a shared environment: separate namespaces in Kubernetes with dedicated node pools, or VPC-per-tenant setups in AWS.
This middle-ground approach suits growing SaaS companies that need stronger security guarantees without the overhead of completely separate deployments.
Every tenant gets completely separate infrastructure: their own cluster, VPC, and potentially even cloud account.
You'll use this for customers with strict compliance requirements (HIPAA, PCI-DSS) or large enterprise contracts that demand physical isolation. The trade-off: you're paying for duplicate control planes and managing multiple clusters.
Real-world production systems often mix these models based on tenant tier. Your standard customers might share infrastructure, while enterprise customers get dedicated deployments.
| Model | Best for | Cost efficiency | Isolation level |
|---|---|---|---|
| Shared | Internal teams, early SaaS | High | Logical |
| Partitioned | Growing SaaS | Medium | Network + compute |
| Dedicated | Enterprise, compliance | Low | Physical |
| Hybrid | Mixed customer tiers | Variable | Flexible |
Northflank provides production-ready multi-tenant environments with built-in isolation, BYOC support, and automated tenant lifecycle management. Deploy multi-tenant applications without spending months on infrastructure complexity.
Get started with Northflank or schedule a demo to see how we can simplify your multi-tenant deployment.
Related resources:
Once you've chosen your deployment model, you need systems to manage the tenant lifecycle, from onboarding new customers to decommissioning old ones.
Manual tenant provisioning doesn't scale. You need infrastructure-as-code that creates all tenant-specific resources automatically: namespaces, databases, secrets, DNS records, and monitoring configs.
Your database strategy significantly impacts deployment complexity. Many production systems use a tiered approach: shared databases for smaller customers, dedicated instances for enterprise tenants.
Each tenant needs isolated configuration: API keys, feature flags, and integration credentials. Modern platforms handle this through projects or workspace abstractions that automatically scope secrets to the right tenants.
Your deployment must enforce network boundaries between tenants through network policies and service mesh configurations with mutual TLS. Platforms like Northflank automate this by provisioning Cilium-based network policies and automatic mTLS when you create new tenant projects.
Multi-tenant deployment introduces operational complexity that doesn't exist in single-tenant systems.
- The blast radius problem: One tenant's misconfiguration or resource spike can crash your entire cluster, requiring aggressive resource quotas and API rate limiting.
- Upgrade and rollout coordination: Deploying updates means coordinating across all tenants simultaneously, requiring canary rollouts and tenant-specific feature flags.
- Cost allocation and chargeback: You need per-tenant resource tracking to allocate costs for internal chargeback or customer billing.
- Monitoring and debugging at scale: You need centralized observability with tenant-scoped views and automated alerting for tenant-specific issues.
- Disaster recovery becomes complex: You need point-in-time recovery per tenant, tenant isolation during restore operations, and the ability to migrate tenants between clusters.
Building and operating multi-tenant deployment infrastructure from scratch typically takes 3-6 months of platform engineering work. Northflank provides production-ready multi-tenant deployment out of the box, letting you focus on your application instead of infrastructure complexity.
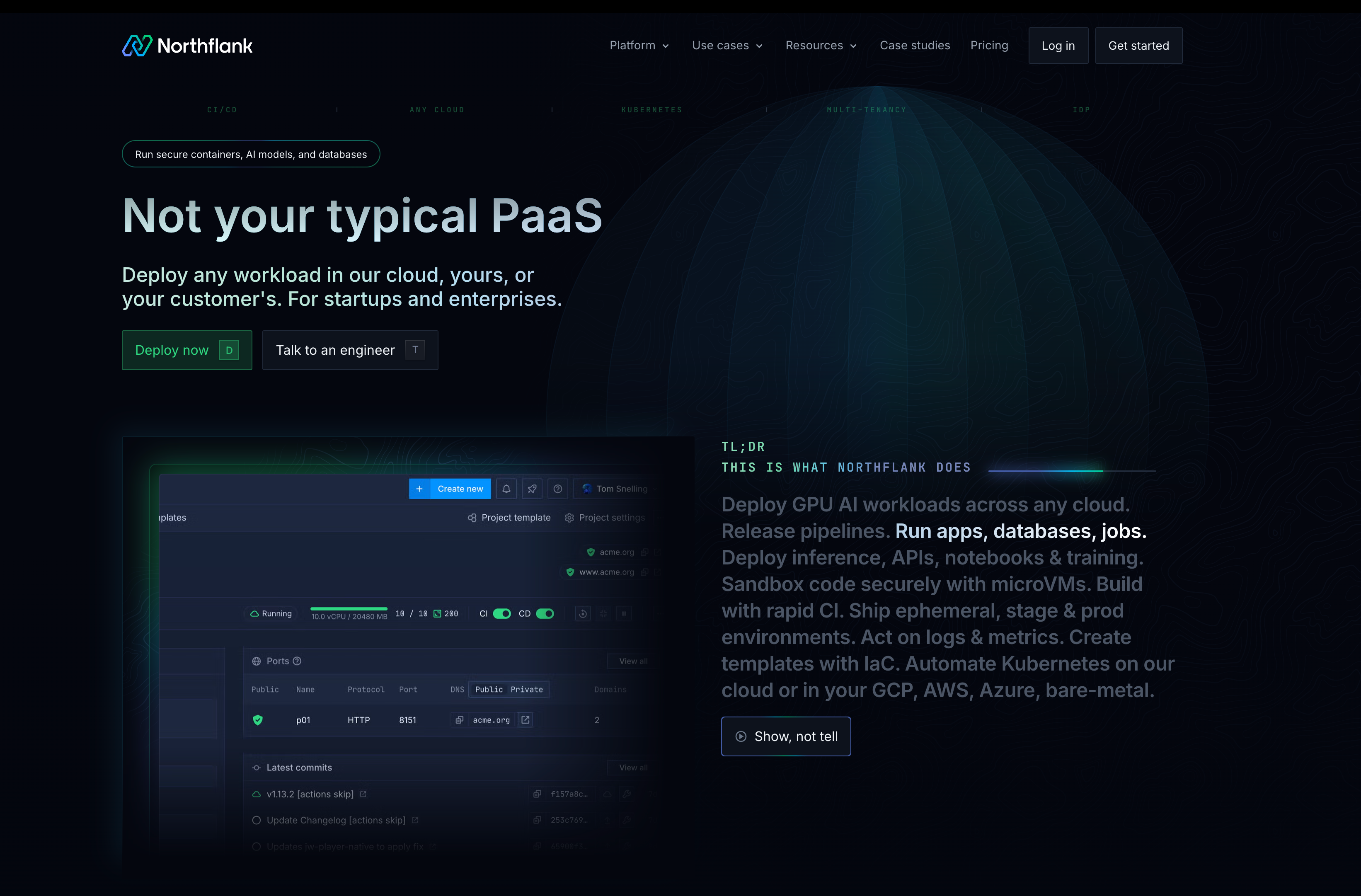
When you create a new project in Northflank, you get an automatically configured tenant environment: dedicated namespaces with network policies, RBAC rules scoped to project members, encrypted secrets storage, and isolated networking with automatic mutual TLS.
You're not writing YAML or configuring network policies manually. Everything is provisioned automatically with production-grade security defaults.
Northflank's Bring Your Own Cloud (BYOC) model lets you deploy multi-tenant systems across AWS, GCP, Azure, Civo, CoreWeave, Oracle, or bare metal, all managed from one control plane.
Your data stays in your VPC, you meet compliance requirements for data residency, and you use existing cloud credits while Northflank handles cluster provisioning, tenant isolation, and ongoing operations.
This is particularly valuable for companies serving enterprise customers who demand data stays in specific regions or clouds.
Northflank handles tenant onboarding, database provisioning, and configuration management automatically. Developers get self-service access to create isolated environments for new customers or projects without waiting for platform team intervention.
Preview environments, managed databases, and GitOps workflows work seamlessly across all tenant projects.
You get per-tenant cost tracking, resource usage monitoring, and audit logs out of the box. No need to build custom solutions for chargeback or debugging tenant-specific issues.
The platform provides unified observability while maintaining tenant isolation, so you can see what's happening across your entire multi-tenant deployment without compromising security.
Focus on these fundamentals before you deploy your first production tenant:
- Start with clear isolation requirements: Understand your compliance and security needs upfront. This determines whether you can use shared infrastructure or need dedicated deployments for certain tenants.
- Automate tenant provisioning from day one: Manual provisioning works for 5 tenants but breaks at 50. Build or adopt automation that handles the full tenant lifecycle before you scale.
- Implement per-tenant monitoring early: You need visibility into resource usage, costs, and performance per tenant. Adding this retroactively to a running multi-tenant system is painful.
- Plan your scaling strategy: Decide how you'll handle vertical vs horizontal scaling in a multi-tenant context, and whether you'll rebalance tenants across infrastructure as you grow.
- The teams that succeed with multi-tenant cloud deployment either build strong platform engineering teams to handle this complexity, or they adopt platforms that provide these capabilities out of the box.
SaaS is a software delivery model where you provide applications over the internet. Multi-tenancy is an architecture pattern where multiple customers share the same infrastructure. Most modern SaaS applications use multi-tenant deployment to serve customers cost-effectively.
The most common patterns are namespace-per-tenant in Kubernetes, VPC-per-tenant for network isolation, and hybrid models that combine shared infrastructure for standard customers with dedicated deployments for enterprise accounts.
Start by defining your isolation requirements, choose your deployment model (shared, partitioned, or dedicated), implement automated tenant provisioning, configure network isolation, and build monitoring for per-tenant resource usage.
A common multi-cloud pattern deploys tenants in different regions across AWS, GCP, and Azure based on data residency requirements. For example, European customers on GCP in europe-west1, US customers on AWS in us-east-1, and Asian customers on Azure in southeast-asia, all managed from a unified control plane.