

Daytona vs E2B in 2026: which sandbox for AI code execution?
- Daytona provides persistent workspaces with container-based isolation and fast cold start performance
- E2B uses Firecracker microVMs for hardware-level isolation with session-based execution
- Core trade-off: Daytona uses Docker containers (faster startup, shared kernel) while E2B uses microVMs (dedicated kernel per session, hardware-level isolation)
- Both platforms operate as managed services where you send your code to their infrastructure
Note: If you need the speed of containers with the security of microVMs, or must keep code execution within your own cloud (AWS, GCP, Azure, Civo, Oracle Cloud, CoreWeave, or on-premise) for compliance, Northflank Sandboxes provides bring-your-own-cloud deployment with Kata and gVisor microVM options and configurable persistence. Unlike managed-only platforms limited to specific cloud providers, Northflank has supported multi-cloud BYOC deployment since inception, giving you full control over where your code executes.
When you're building AI agents that execute code, the sandbox platform you choose determines how you balance security, performance, and persistence.
These platforms represent two different philosophies for handling AI-generated code:
- Daytona approaches sandboxing from a developer workspace perspective, focusing on persistent environments where your agent can build up state over time
- E2B focuses specifically on running untrusted code from LLMs with hardware-level isolation boundaries
Understanding these architectural differences helps you choose based on your isolation requirements, session persistence needs, and deployment constraints.
If you're new to sandboxing concepts, this guide on what an AI sandbox is provides essential context for evaluating these platforms.
Daytona is a development environment platform that provides workspaces for developers and AI agents.
The platform focuses on persistent environments where code, dependencies, and files remain available across sessions.
Daytona uses Docker containers as its isolation technology, prioritizing startup speed and resource efficiency.
E2B is a platform built specifically for executing untrusted code from AI agents.
The platform uses Firecracker microVMs, the same virtualization technology that powers AWS Lambda.
Each code execution runs in its own kernel, providing isolation at the hardware level rather than just the process level.
The fundamental difference lies in how each platform approaches isolation and persistence.
Daytona provides stateful workspaces where your AI agent can install dependencies, create files, and return to the same environment later. The platform uses containers that share the host operating system kernel.
E2B provides execution environments that run in dedicated microVMs. Each execution gets its own kernel, preventing kernel-level exploits from affecting other executions or the host system.
| Feature | Daytona | E2B |
|---|---|---|
| Isolation technology | Docker containers | Firecracker microVMs |
| Kernel isolation | Shared host kernel | Dedicated kernel per session |
| Session persistence | Configurable, long-term | Session-based |
| Primary use case | Persistent development workspaces | Ephemeral code execution |
| Deployment model | Managed or self-hosted | Managed service |
Need deployment flexibility, speed, and security?
Both Daytona and E2B operate as managed services where your code executes on their infrastructure.
If you need to keep code execution within your own infrastructure or require hardware-level isolation beyond standard containers, Northflank Sandboxes supports bring-your-own-cloud deployment to AWS, GCP, Azure, Civo, Oracle Cloud, CoreWeave, or on-premise servers.
Daytona treats sandboxes as long-lived workspaces rather than disposable execution environments.
When your AI agent installs a Python package or creates a configuration file in a Daytona workspace, that change persists. The next time your agent connects to the same workspace, the installed packages and created files remain available.
This persistence model suits AI agents that need to:
- Build up a working environment over multiple interactions
- Store generated code across sessions
- Maintain installed dependencies without reinstalling them
- Keep project files and artifacts available
An AI coding assistant that helps refactor a large codebase might work across multiple sessions, building on previous changes each time. Teams building AI agents that manage projects or maintain state across multiple user interactions typically need persistence.
Understanding how to sandbox AI agents helps you design these architectures based on your requirements.
E2B uses Firecracker microVMs to provide hardware-level isolation for each code execution.
Each code execution runs in its own microVM, which means it gets a dedicated Linux kernel. This kernel-level isolation prevents exploits that rely on shared kernel vulnerabilities, such as container escape attacks that target the host operating system.
When you run code generated by an LLM, you're executing potentially malicious instructions. The code might attempt to:
- Access sensitive files on the host system
- Exploit kernel vulnerabilities to escalate privileges
- Attack other processes running on the same machine
- Exfiltrate data from adjacent workloads
Firecracker microVMs prevent these attacks by isolating each execution at the virtualization layer. This isolation level meets compliance requirements for organizations handling sensitive data.
When evaluating the best code execution sandbox for AI agents, compliance teams often require hardware-level isolation rather than container-level boundaries.
The isolation technologies operate at different layers of the system stack.
Docker containers (used by Daytona) isolate processes using Linux kernel features like namespaces and cgroups. Multiple containers share the same kernel, which means kernel vulnerabilities could potentially allow an attacker to escape container boundaries.
Firecracker microVMs (used by E2B) provide each execution with its own kernel. Kernel exploits inside one microVM cannot affect other microVMs or the host because the isolation happens at the hardware virtualization layer.
| Isolation aspect | Docker containers (Daytona) | Firecracker microVMs (E2B) |
|---|---|---|
| Kernel sharing | Shared across containers | Dedicated per microVM |
| Escape prevention | Relies on kernel security | Hardware-enforced boundaries |
| Boot overhead | Minimal | Higher |
| Security boundary | Process-level | Hardware-level |
| Compliance suitability | Depends on requirements | Meets strict requirements |
If you're implementing your own isolation stack, this guide on how to spin up a secure code sandbox with Firecracker, gVisor, and Kata shows you the technical requirements.
Cold start performance affects the responsiveness of your AI applications.
Daytona's container-based approach provides faster cold starts because containers only need to initialize namespaces and mount filesystems. E2B's microVMs need to boot a minimal Linux kernel, which takes longer despite Firecracker's optimizations.
For most AI code execution use cases, both platforms provide acceptable performance. The performance difference matters most for applications that create thousands of short-lived sandboxes per minute.
Need both speed and security?
Running untrusted code in production often requires hardware-level isolation beyond what standard containers provide.
If you need microVM security (Kata or gVisor) with configurable persistence and deployment options, Northflank Sandboxes offers isolation technologies that you can run in your own cloud environment, giving you the security benefits of microVMs while maintaining control over your infrastructure.
Both platforms provide SDKs with different design philosophies.
| Aspect | Daytona SDK | E2B SDK |
|---|---|---|
| Primary focus | Workspace lifecycle management | Code execution with minimal setup |
| Language support | TypeScript/JavaScript, Ruby, Go | Python, TypeScript/JavaScript |
| Best suited for | Complex workflows with dependencies, multiple commands, state maintenance | Straightforward code execution without workspace management |
Kubernetes integration affects how these platforms fit into your existing infrastructure.
Daytona and Kubernetes: Daytona provides Helm charts for Kubernetes deployment, but the setup uses Docker containers (not microVMs) and requires manual cluster management. While some BYOC options may exist, they're not publicly documented or self-serve.
E2B and Kubernetes: E2B operates primarily as a managed service. Their self-hosting uses Nomad for orchestration and supports AWS and Google Cloud environments. Like Daytona, any BYOC capabilities are not easily accessible or self-serve.
For teams that need self-serve bring-your-own-cloud deployment without sales negotiations, this guide on top AI sandbox platforms for code execution compares options designed for accessible BYOC.
Your choice depends on how you balance persistence, isolation, and deployment requirements.
| Use case | Daytona | E2B | Northflank Sandboxes |
|---|---|---|---|
| Session persistence | Extended workspace duration, multi-session projects | Session-based execution | Configurable persistence based on workflow needs |
| Isolation technology | Docker containers (shared kernel) | Firecracker microVMs (dedicated kernel) | Choice of Kata, gVisor, or Firecracker microVMs |
| Performance | Fast cold starts | Optimized microVM boot times | Configurable based on isolation choice |
| Deployment model | Managed or Helm charts (Docker only, BYOC not self-serve) | Managed service (BYOC not self-serve, AWS/GCP) | Managed PaaS, self-serve BYOC (AWS, GCP, Azure, Civo, Oracle, CoreWeave), or on-premise |
| Kubernetes orchestration | Helm charts available, requires manual setup | Not supported (uses Nomad) | Self-serve BYOC with managed K8s |
| Infrastructure control | Limited, manual configuration required | AWS/GCP managed infrastructure | Full control in your own environment or managed |
| Best for | Long-running AI agent projects, stateful development | AI chat code interpreters, untrusted LLM code | Compliance-focused teams, data sovereignty, enterprise requirements |
If you need to keep AI code execution within your own infrastructure or require flexibility beyond what Daytona and E2B provide, Northflank addresses these constraints.
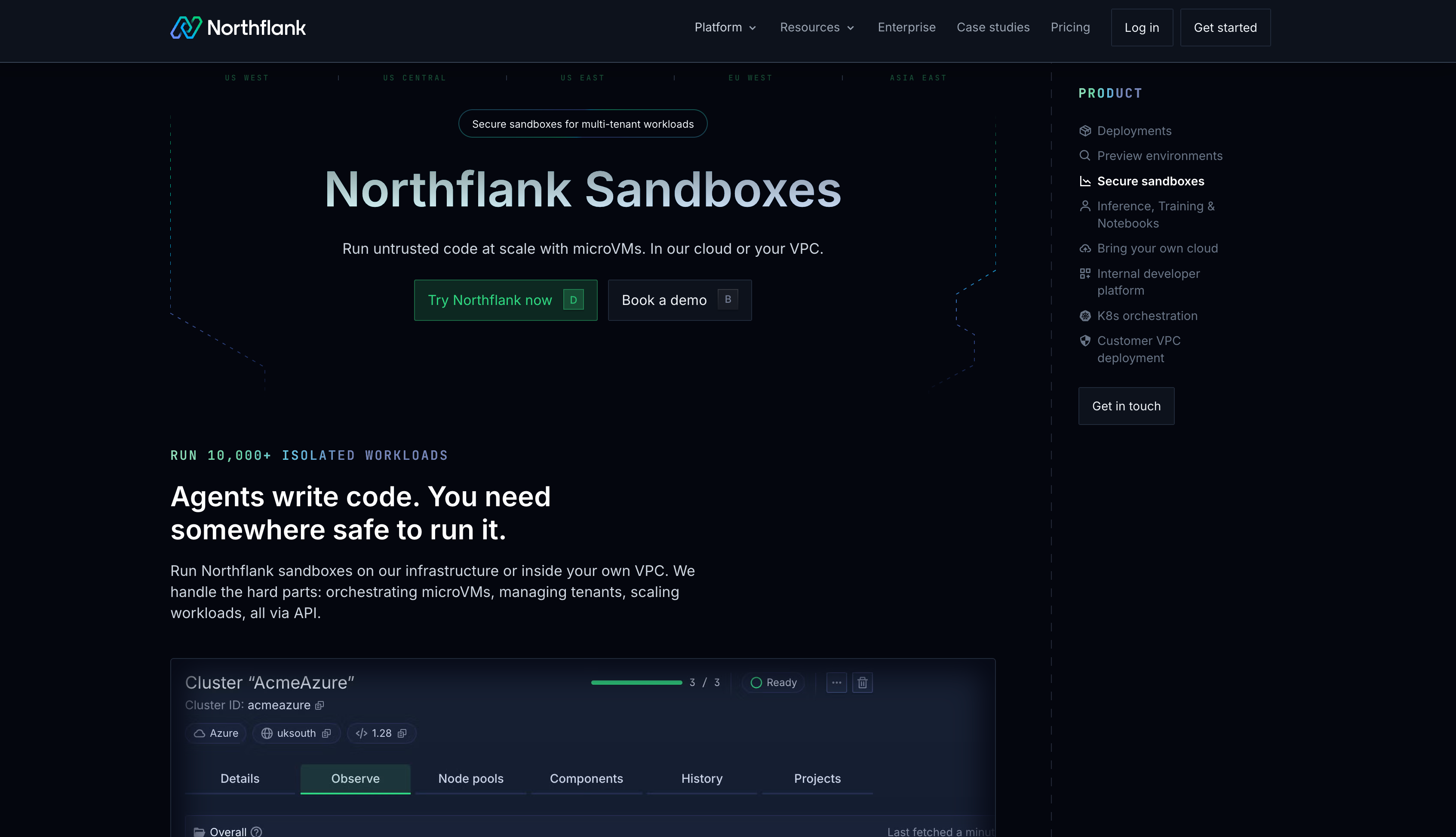
What Northflank offers:
- Deployment flexibility: Choose between managed PaaS or bring-your-own-cloud deployment to AWS, GCP, Azure, Civo, Oracle Cloud, CoreWeave, or on-premise servers
- Advanced isolation options: Select between Kata Containers, gVisor, or Firecracker microVMs based on your security requirements
- Configurable persistence: Set session duration based on your workflow requirements without platform-imposed limits
- Kubernetes-native orchestration: Integrates with your existing K8s clusters, security policies, and RBAC
Northflank targets compliance-focused teams and organizations with data sovereignty requirements that prevent using external managed services.
Get started with Northflank:
Learn more about Northflank Sandboxes or read our guide on self-hosted AI sandboxes for your infrastructure. For production workloads, see how to implement secure AI code execution at scale.
Compare best alternatives to E2B and top Daytona alternatives based on your specific requirements.
Daytona provides persistent container-based workspaces, while E2B provides Firecracker microVM environments. Daytona prioritizes stateful development environments while E2B prioritizes hardware-level security. For teams needing both, Northflank Sandboxes offers configurable options.
E2B provides stronger isolation through Firecracker microVMs with dedicated kernels. Daytona uses Docker containers with shared host kernels. MicroVM isolation reduces risk when running LLM-generated code.
Both platforms offer self-hosting with limitations. Daytona's Helm charts deploy Docker containers and require manual Kubernetes management. E2B's self-hosting uses Nomad and supports only AWS and Google Cloud. While both may offer BYOC options, these are not easily accessible or self-serve. Northflank provides self-serve, production-ready BYOC deployment with managed Kubernetes orchestration across AWS, GCP, Azure, Civo, Oracle Cloud, CoreWeave, and on-premise infrastructure.
Container isolation suits trusted code in non-critical applications. MicroVM isolation (Firecracker, Kata, gVisor) is required for untrusted code in production, especially when meeting compliance standards like SOC2 or HIPAA.